The Incident Response Life Cycle: What You Need to Know
 Modern organizations’ threats have never been more varied and potentially more damaging. Mitigating these threats is always the first line of defense, but what happens if an attacker makes it past your defenders?
Modern organizations’ threats have never been more varied and potentially more damaging. Mitigating these threats is always the first line of defense, but what happens if an attacker makes it past your defenders?
From a time and investment perspective — response planning is equally as critical as incident prevention. IBM’s Cost of a Data Breach Report 2023 revealed that most companies take 197 days to identify a breach and 69 days to contain it — resulting in millions of dollars in damages and lost revenue. What’s clear: responding to breaches is the new reality and having an organized and effective response can make a difference in your recovery.
Incident response planning is an organized approach to addressing and managing the aftermath of a successful attack or other incident that disrupts business continuity. While the focus of incident responses is often cyber attacks, be aware that everything from natural disasters to supply chain issues should be considered during the incident planning phase.
Your incident response plans aim to minimize the damage, reduce time to recovery, and identify ways to prevent future incidents from occurring.
What does an incident response look like in practice? While there are unique challenges and varying plans based on the type of incident, they’ll almost always follow the same lifecycle.
So, keep reading a refresher of what this life cycle looks like, and how your organization can prepare to minimize the impact of any given incident before it harms the bottom line.
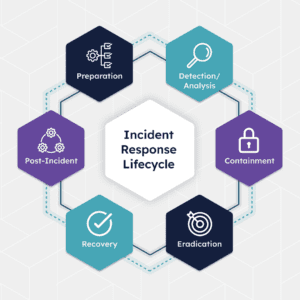
The Phases of the Incident Response Life Cycle
The incidents you need to respond to can vary dramatically from one another when it comes to the root cause. However, you’ll follow the same overall life cycle for nearly all of them. We’ll break down each phase’s incident response life cycle in the typical sequential order.
1. Preparation
The incident response life cycle begins before an incident occurs during the preparation phase. During this phase, you’ll develop and refine incident response plans and protocols to ensure you have the right people and platforms to recover.
It’s not usually possible to develop step-by-step responses for every scenario, so instead, focus on overarching procedures to follow. For example, communication and documentation are two of the most important elements in rapidly recovering from anything from a data breach to a power outage.
If you depend on internal systems to recover from a system failure, you’ll quickly find printed documents and inefficient call trees. Instead, develop procedures for when to switch to out-of-band communications so your teams can collaborate in an environment that’s segmented from your primary networks.
This same principle applies to every procedure and broadly across various incidents, such as evidence collection and impact prioritization. Prepare these processes beforehand, so your teams know what to do when an incident occurs.
2. Identification
The life cycle of a specific incident begins before you identify it and continues until it’s fully resolved. If a cybersecurity breach remains undetected, the response can’t begin.
Here’s what we know: nearly 33% of breaches go undetected by IT and security professionals.
Monitoring your entire IT ecosystem and supporting infrastructure is critical to identifying an incident. Fortunately, advanced tools exist to monitor for any signs of unauthorized access or anomalous behavior.
SIEM, IDS endpoint protection solutions are standard for signature-based detection, yet threats like unpredictable fileless and in-memory attacks can evade detection — delaying response and potentially inflicting greater damage. Anticipating predictable and unpredictable events supports cyber resiliency. At the offset of any event, your teams can enact response playbooks and switch to your incident response virtual bunker to support an organized and tactical response.
Once identified, your teams can start responding to them accordingly. They can switch to your incident response virtual bunker for secure communications and collaboration to enable faster response and minimize the incident’s impact.
 3. Containment
3. Containment
Now that you know the incident has occurred, your teams can begin working to contain it and limit its impact on your organization. Immediate goals typically focus on isolating affected systems and securing sensitive data to mitigate possible losses.
Several specific containment strategies depend on the specific incident and often have short-term and long-term elements. For example, a short-term strategy might disconnect impacted machines from the network, while long-term strategies focus on changing access controls or system configurations.
Having predefined plans for containment based on the type of incident is a foundational best practice that enables rapid response, reducing scope and severity.
Tip: Ensure your containment efforts aren’t visible to adversaries. Having an out-of-band solution detached from your primary network allows you to safely store playbooks and enable communications without fear of sabotage or exploitation.
4. Eradication
You’ve contained the incident — now it must be eradicated. This phase is focused on completely removing the threat from your IT environment or otherwise affecting the business.
Eradication might focus on eliminating malware, patching security vulnerabilities being exploited, or revoking compromised credentials. In the case of incidents other than cyber attacks, eradication might look like switching to power generators and ensuring they have enough fuel, for example.
However, it’s important not to unnecessarily dive into root cause analysis during eradication. You won’t always have this luxury, but the focus should remain on what is currently enabling the incident to continue and removing it. True root cause analysis is essential but occurs during the post-incident review.
Tip: Ensure event logs continue to store data through resolution. This is critical for things like cyber insurance and compliance reporting.
5. Recovery
The active threat has been deactivated; now it’s time to recover to normal business operations. This process often involves carefully reintroducing downed systems and carefully monitoring them to make sure there are no lingering threats.
Recovery focuses on returning affected systems to their original state while thoroughly ensuring that the incident has actually been resolved.
The timeline for recovery can vary dramatically based on the severity of the incident and the effectiveness of the earlier response phases. Having detailed plans and backup communications in place can go a long way toward minimizing the impact and enabling faster recovery.
6. Post-Incident Review
The final phase of the incident response life cycle is the review period. This step occurs once the threat has been eliminated and the recovery process has been completed.
The post-incident review focuses on refining incident response plans and better preparing for future threats. Teams and leaders will review a detailed breakdown of the incident, how it was handled, and identify ways the response could’ve gone better.
Reviewing the incident is what forms the cyclical aspect of the life cycle. The same type of incident may occur, so reviewing results aims to ensure it is resolved faster next time — or mitigated entirely.
Tip: Keep your playbooks updated while continuing to tune response plans with greater detail by activity through the entire lifecycle. Map out the time required to complete each response task. This helps with internal KPIs, benchmarks, sets realistic expectations for leadership, and response team training.
Enable Faster Incident Responses with ShadowHQ
A wide range of scenarios threaten your ability to operate, harming your reputation and disrupting revenue. Identifying, containing, and eradicating these threats as quickly as possible is critical to minimize their impact, including how much they cost your business.
Equipping your teams with easy access to incident response playbooks alongside secure, out-of-band communications is of the utmost importance.
ShadowHQ is an industry-leading provider of secure communications and document storage that will not be affected by threats to your day-to-day systems. Detached by design, our incident response bunker lets your teams collaborate on each incident response life cycle step and get back up and running securely.
Could your incident response plan benefit from out-of-band communications and document storage? Schedule a demo today to learn more about our virtual bunker to help you respond to any incident.
EWEBINAR
Experience the ShadowHQ platform
Walk through a cyber breach scenario in a 15 minute demo.
GUIDE DOWNLOAD
Disaster Readiness Checklist
When an emergency happens, every minute counts.


