Essential Guide to Managing an Active Incident Effectively
7 Practical Tips to Improve Your Active Incident Cybersecurity Response
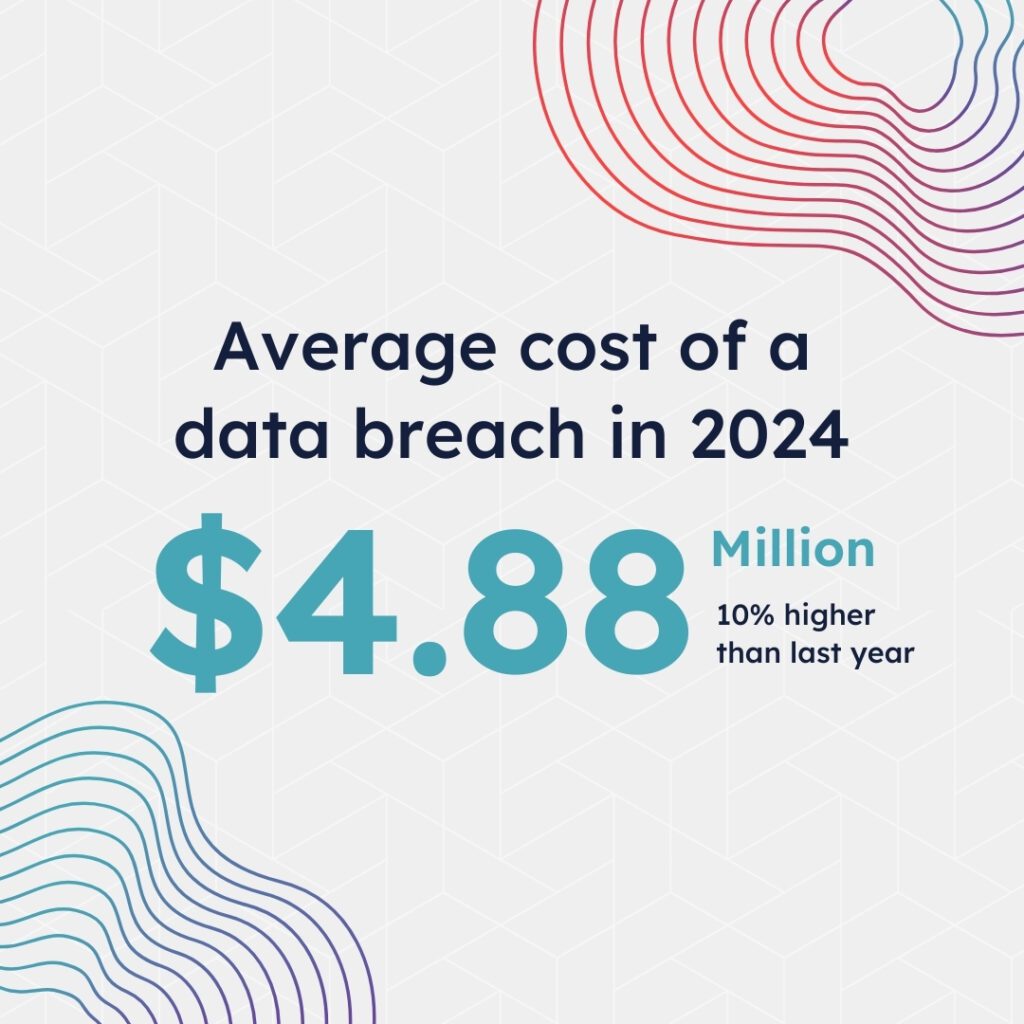
Cyber attacks have become increasingly common and costly. In the first quarter of 2024, there were 9,478 publicly disclosed incidents — more than 100 per day. At the same time, an IBM study found that the average cost of a data breach in 2024 is US$4.88 million, 10% higher than last year.
Improving cybersecurity incident responses greatly mitigates the impact of a successful attack. Having accurate and timely information regarding incidents is crucial for detecting, containing, and eradicating an attack before it can siphon off a wealth of data, thereby reducing its cost to your business, both directly and indirectly.
So, how can you improve your cybersecurity incident responses? We’ll be breaking down seven ways to enhance how you detect, respond to, and resolve a cyber incident before it becomes more severe and costly — read on to create a more resilient business.
1. Be Aware of Possible Incidents that Can Occur with Risk Assessments
What threats face your organization? What vulnerabilities are you aware of that may enable a successful attack?
Risk assessments must be conducted quarterly or annually so that you’re fully aware of your business’s threats and vulnerabilities. Additionally, security teams should stay on top of emerging threats facing your industry, such as a new attack vector growing in popularity. Being aware of active incidents is crucial as they can significantly impact your organization.
Knowing these risks directly informs developing incident response plans, types of drills to practice, and refining overarching protocols like how to communicate during an attack.
2. Create Thorough Cyber Security Incident Response Plans
Do you have established response plans for known cybersecurity incidents? Do they include protocols and tools that allow teams to effectively contain, eradicate, and recover from a successful attack?
The risk assessment process discussed earlier helps you understand possible cyber attacks facing your organization. Most organizations then focus on risk mitigation strategies, which is necessary, but don’t overlook creating incident response plans in case mitigation strategies fail. Including root cause analysis in these plans is crucial for quickly diagnosing and resolving incidents.
Security teams should be prepared to handle a successful attack and not be required to develop solutions during an active incident.
3. Evaluate All Existing Response Processes
What are your current cybersecurity incident response processes? Do you need to establish new cybersecurity response plans, or do you have an existing program? Are you prepared to respond to alerts from monitoring systems to stop the attack before it affects the business?
Establishing, maturing, and refining cybersecurity response plans is an ongoing process that should be conducted at pre-defined intervals, such as quarterly or annually. Additionally, should an incident occur, post-incident review processes will likely inform changes to incident response plans and mitigation strategies. It is crucial to have a dedicated page for detailed reports or dashboards related to incidents, ensuring structured organization and easy access to relevant information.
4. Provide Thorough Training to All Employees
More and more, employees in non-technical departments are targeted by bad actors to gain access to IT assets. Provide all employees with ongoing training to identify and prevent these attacks, regardless of their department.
Phishing and social engineering, for example, are two common attacks that target sales, marketing, or human resources to manipulate the human element to enable an attack.
Additionally, should an attack be successful, training for technical and non-technical teams in their roles during an incident is highly valuable. Sales teams won’t be involved in the direct response, but how should they communicate with customers if an incident becomes public-facing?
5. Establish Backup Communication Channels and Protocols
Several possible cyber attacks can bring down communications or compromise them. Even if still online, you don’t want an attacker eavesdropping on how you plan to respond to the incident.

Developing communication protocols for incidents, including out-of-band communication channels, keeps teams communicating and collaborating far from eavesdropping. These cloud-based tools allow teams to stay in real-time contact as they work to contain and recover from an incident.
While adopting a new platform for backup communications represents a new investment, resolving incidents faster thanks to communications reduces their impact, creating a positive ROI in the process
6. Test, Refine, and Update Response Plans Regularly
Don’t wait until an active incident to gauge the effectiveness of established incident response plans. Run drills that test them using simulations or tabletop drills to find weaknesses or deficiencies. You’ll then be able to refine response plans to give them the best chance of success should an incident occur.
Beyond tests and refinements, plans should also be regularly reviewed for technical and strategic accuracy. The cybersecurity landscape never rests, so plans need to be updated as attacks and defenses change.
7. Adopt the Right Incident Response Tools
An effective response to a cyber attack requires the right process, people, and platforms to contain and eradicate the threat and restore affected services. Missing one of these three elements, such as lacking the right technologies, can reduce the effectiveness of the entire incident response plan.
Evaluate plans with a focus on available tools. Do your existing tools offer what teams need to succeed? Or are there tools on the market that would improve existing plans?
Make sure response teams are prepared with the right platforms and training in how to use them during an incident to effectively detect and contain an incident before it becomes more severe.
Is Your Organization Ready to Respond to Cyber Attacks?
Cyber incidents have grown in frequency and costs. The first line of defense is to prevent them entirely, but are you ready to respond if an attacker gets through those defenses?
Establishing and continually improving cybersecurity incident response plans with the right incident response software, processes, and teams in place helps your organization better detect and eradicate attacks.
ShadowHQ has everything you need to plan and recover fast — whether that’s helping you support all your business’s stakeholders, boosting visibility when it matters most, or providing control and collaboration during a crisis. As the incident response lead, ShadowHQ simplifies your job, allowing you to pre-load your response plans, contact lists, and response playbooks to support a faster response and recovery while minimizing damage and overall business impact.
How prepared is your business to respond effectively to a cyber attack? We’ve put together a disaster readiness checklist to help gauge your existing processes and start improving them — check out our disaster readiness checklist today.
EWEBINAR
Experience the ShadowHQ platform
Walk through a cyber breach scenario in a 15 minute demo.
GUIDE DOWNLOAD
Disaster Readiness Checklist
When an emergency happens, every minute counts.


