Top 5 Crisis Management Platforms to Enhance Your Emergency Response
Crisis Management Platform: How Technology Is Shaping the Future of Cyber Crisis Management
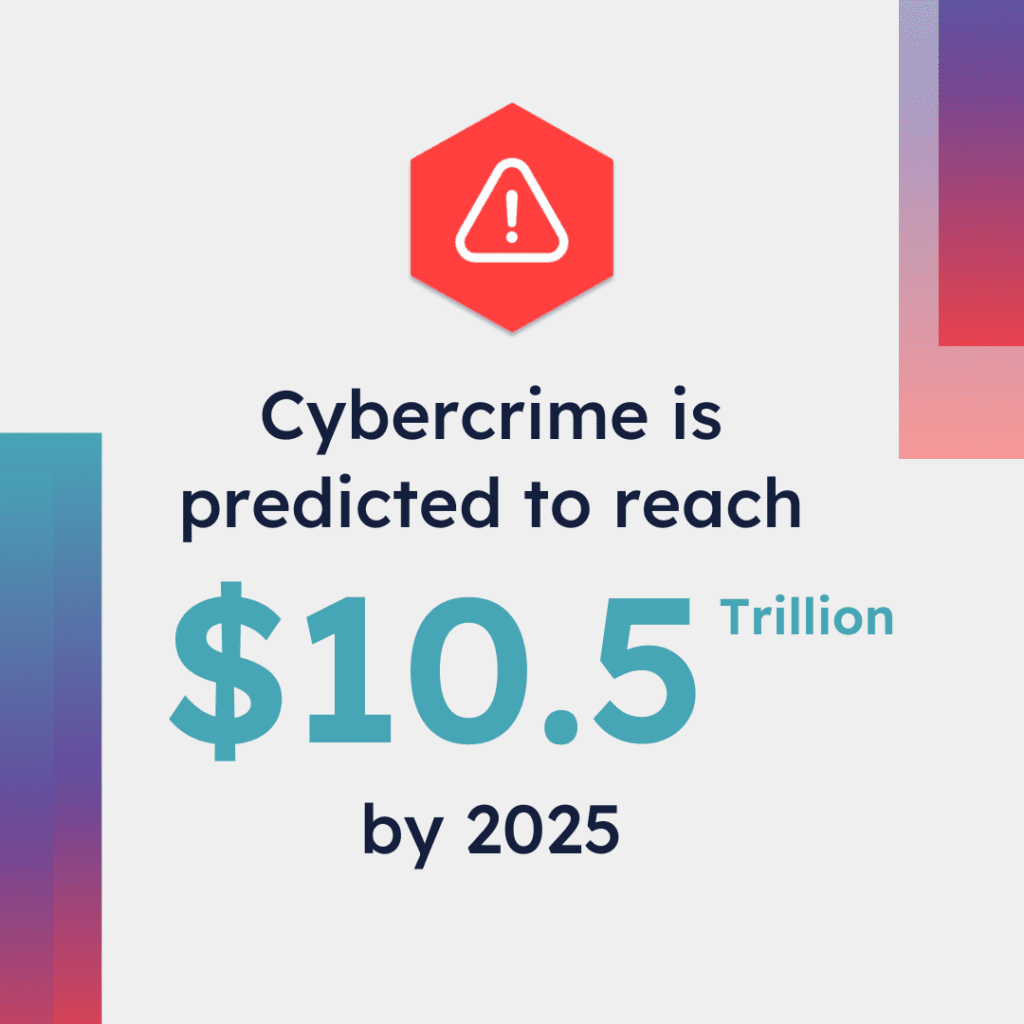
Cyber crisis management has been top of mind in recent years as the cost of cyber attacks has increased. One study shows the cost of cybercrime is predicted to reach US$10.5 trillion by 2025, speaking to the volume and business risks of these crises.
Additionally, according to the IBM Cost of a Data Breach Report 2023, the average cost of a data breach rose to $4.45 million, and in 2023, 83% of surveyed organizations had experienced more than one data breach.
A single risk can have far-reaching consequences, from compliance fines, loss of consumer trust, and reputation damage throughout the industry. Cyber crisis management is increasingly necessary to prevent or minimize the impact of cyber attacks.
Identifying threats, implementing mitigation controls, and having ready-to-go incident response plans are critical to preventing costly attacks. The cyber crisis management market was valued at US$3.9 billion in 2023 to $53.3 billion in 2033, a substantial increase largely attributed to the increase in risks of cyber crisis.
Technology is at the core of both the risks facing companies and the tools available to prevent them. Organizations are spending more than ever, and the cost of failing to do so has never been greater.
Many businesses rely on manual methods for crisis management, while others have adopted technologies like crisis management tools to streamline processes.
The reality is that with the likelihood of a cyber breach event rising — all businesses need to re-evaluate and augment their crisis management processes to ensure a speedy recovery while minimizing damage. Having a robust crisis strategy is essential to manage risks and improve responses, ensuring resilience and preparedness in the face of unexpected challenges.
So, how might cyber crisis management change as technologies continue to evolve? We’ll be exploring several critical trends in technology, look at how they’ll shape the future of cyber crisis management, and how you can integrate them within your organization’s crisis response planning.
Understanding Crisis Management
Crisis management is a cornerstone of business continuity and emergency preparedness. It involves identifying, assessing, and mitigating risks that could disrupt an organization’s operations, reputation, or financial stability. Effective crisis management requires a proactive approach, including the development of a comprehensive crisis management plan, the establishment of a dedicated crisis team, and the implementation of advanced crisis management software.
A crisis management plan is a detailed document that outlines the procedures and protocols for responding to a crisis. It should identify potential risks, establish a crisis team, and develop communication strategies for key stakeholders. The plan must also include procedures for responding to critical events, such as natural disasters, workplace violence, or negative sentiment on social media channels. By having a well-structured crisis management plan, organizations can ensure they are prepared to handle any situation that arises, maintaining business continuity and protecting their reputation.
AI and ML Technologies: The Double-Edged Sword
Artificial Intelligence (AI) and Machine Learning (ML) are behind some of the most transformative technologies facing cyber crisis management. Enterprises can benefit from advanced threat detection, AI-powered risk mitigation, and data-driven insights to inform crisis management programs. Additionally, social listening plays a crucial role in monitoring online conversations and identifying potential threats in real-time, allowing brands to respond swiftly to crises and manage their online reputation effectively.
Unfortunately, the ongoing AI transformation doesn’t just benefit cybersecurity — malicious actors are leveraging generative AI to create and execute sophisticated attacks. From social engineering to coding malware, generative AI represents an entirely new landscape of threats with a lower barrier to entry for would-be attackers.
Both blades of the AI sword are shaping cyber crisis management. New aides can help prevent and respond to incidents while creating new threats that must be considered. Risk assessments must be conducted more frequently to identify and create management plans for emerging threats.

Growing Utility of Secure Cloud-Based Recovery Platforms for Business Continuity
What do you do if an incident takes down a significant amount of your infrastructure? In the past, this meant scrambling to find paper versions of response plans and relying on other methods like manual call trees.
Now, cloud-based recovery platforms have created a new range of tools to help ensure business continuity and enable faster crisis recovery. Platforms like ShadowHQ create a backup method to ensure communication, collaboration, and storage of response plan documents.
One critical aspect of cyber risk and crisis management is mitigating the impact of a successful breach. For example, if a bad actor compromises an employee’s credentials, the more they can move through the system — the costlier and more damaging the breach.
Other technologies aim to prevent breaches and restrict movement, while rapid recovery helps get all hands on deck to stop and recover from the incident. Having a cloud-based recovery platform as part of your crisis management program can go far in minimizing the cost of a cyber attack. Swiftly notifying response teams and maintaining open communication lines during incidents are crucial for effective crisis management.
Crisis Management Software
Crisis management software is an essential tool for organizations to effectively manage and respond to crises. It provides a centralized platform for crisis teams to collaborate, communicate, and address critical events. This software typically includes features such as incident reporting, team activation, situational awareness, and crisis communication, all of which are crucial for a coordinated response.
When selecting crisis management software, organizations should consider several factors:
-
Ease of Use: The software should be user-friendly and intuitive, even for non-technical users.
-
Customization: It should be customizable to meet the specific needs of the organization.
-
Integration: The software should seamlessly integrate with existing systems and tools, such as social media channels and news sites, to provide a comprehensive view of the situation.
-
Scalability: It should be scalable to accommodate the organization’s size and complexity.
-
Security: Robust security features are essential to protect sensitive information and ensure data integrity.
By choosing the right crisis management software, organizations can enhance their crisis response capabilities, ensuring they are well-prepared to handle any critical event.
Advanced Training Simulations for Crisis Communication
New virtualization technologies have enabled enterprises to simulate attacks and execute response plans in a contained environment. Rather than waiting for attacks to occur for hands-on experience, virtual environments allow new and experienced team members to work through crisis management plans to prepare for the real thing.
Additionally, managers and stakeholders can review how teams enact crisis management plans and practices, which may help identify areas for improvement. Reputation management is crucial in protecting a brand during negative situations and ensuring effective crisis responses.
Another benefit of advanced simulations is providing cybersecurity training to other teams and departments that are not directly involved in crisis management but may enable an attack. For example, creating scenarios that employees may face will help them better identify phishing and social engineering attacks.
Cybersecurity Mesh Rather Than Fortress
Cyber crisis management aims to mitigate attacks and prepare organizations to respond effectively should an incident occur. A series of trends and technologies have moved the focus of mitigation away from the long-time “defend the fortress” perspective.
Now, devices located in and out of the office must be protected. This new landscape has shifted the focus to a cybersecurity mesh perspective, with each endpoint requiring robust security.
Cybersecurity mesh isn’t a specific technology but rather a collection of multiple technologies, such as zero trust architecture, MFA, and end-to-end encryption, to name a few. The goal is to enable enterprises to better protect individual devices while limiting the movement of compromised credentials.
Quantum Computing Threatens Encryption
Quantum computing, an entirely new form of computing, has already made significant breakthroughs, with some quantum computers with a limited number of qubits finding specialized use cases. While plenty of development is still necessary before it is widely available, quantum computing is being taken seriously by many in the industry and should be on enterprises’ radar.
So, what’s the threat? Once a certain stage of development is reached, quantum computers will be capable of breaking most forms of encryption due to its fundamental change in computing.
Cyber crisis management programs need to stay on top of post-quantum encryption (PQE) standards as they emerge. NIST is currently formalizing several new encryption standards believed to be quantum-resistant. Four algorithms have been chosen and will soon be formalized in upcoming standards.
For now, enterprises won’t likely need to take action. However, adopting PQE tools as they emerge will go far in ensuring ongoing security as quantum computing continues to advance.
Business Continuity Planning
Business continuity planning is the process of identifying and mitigating risks that could disrupt an organization’s operations. It involves developing a business continuity plan, which outlines the procedures and protocols for responding to a crisis and ensuring the organization can continue to function.
A comprehensive business continuity plan should include the following components:
-
Risk Assessment: Identifying potential risks that could disrupt operations.
-
Business Impact Analysis: Assessing the potential impact of a crisis on the organization.
-
Crisis Management Plan: Developing a crisis management plan that outlines the procedures and protocols for responding to a crisis.
-
Communication Plan: Creating a communication plan that details how to communicate with key stakeholders during a crisis.
-
Training and Testing: Regularly training and testing the crisis management plan to ensure its effectiveness and efficiency.
By developing and maintaining a robust business continuity plan, organizations can ensure they are prepared to respond to a crisis, minimizing the impact on their operations and reputation. This proactive approach to crisis management is essential for maintaining business continuity and safeguarding the organization’s future.
Make ShadowHQ Part of Your Cyber Crisis Management Program
Cyber crisis management has never stood still, and it’s not about to start. Several current and future technologies create even more dramatic changes that enterprises must consider as they bolster cyber security and create resilient recovery plans.
ShadowHQ offers a secure command center for teams to collaborate and communicate during crises. Our platform allows prioritized task management, secure communications, and backup storage for critical documents. When it comes to cyber crisis management, the platform can help you:
-
Keep all stakeholders in the loop during any crisis.
-
Rapidly restore critical business functions.
-
Enhance communications to help recover, outside of possibly affected infrastructure.
-
Equip your team with a secure command center to collaborate and recover.
-
Define roles within ShadowHQ so everyone knows what tasks they own.
As technologies emerge, bolstering your cyber crisis management programs has never been more critical. Are you ready to step up how you manage and recover from crises? Book a demo today to discover how ShadowHQs secure command center can help today, and download the Disaster Readiness Checklist for tips to improve your incident preparedness processes.
EWEBINAR
Experience the ShadowHQ platform
Walk through a cyber breach scenario in a 15 minute demo.
GUIDE DOWNLOAD
Disaster Readiness Checklist
When an emergency happens, every minute counts.


